Refer to the exhibit.
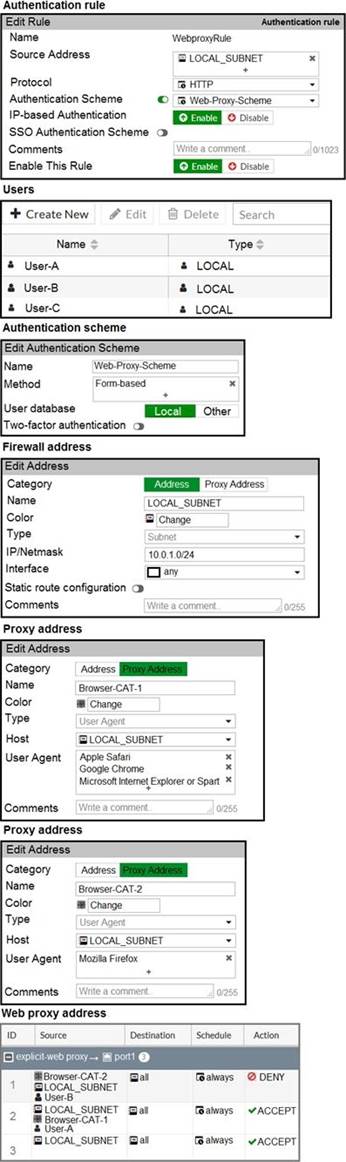
The exhibit shows proxy policies and proxy addresses, the authentication rule and authentication scheme, users, and firewall address.
An explicit web proxy is configured for subnet range 10.0.1.0/24 with three explicit web proxy policies.
The authentication rule is configured to authenticate HTTP requests for subnet range 10.0.1.0/24 with a form-based authentication scheme for the FortiGate local user database.
Users will be prompted for authentication.
How will FortiGate process the traffic when the HTTP request comes from a machine with the source IP 10.0.1.10 to the destination http://www.fortinet.com? (Choose two.)
A . If a Mozilla Firefox browser is used with User-B credentials, the HTTP request will be allowed.
B . If a Google Chrome browser is used with User-B credentials, the HTTP request will be allowed.
C . If a Mozilla Firefox browser is used with User-A credentials, the HTTP request will be allowed.
D . If a Microsoft Internet Explorer browser is used with User-B credentials, the HTTP request will be allowed.
Answer: A,D

Leave a Reply