Robin, a professional hacker, targeted an organization’s network to sniff all the traffic.
During this process.
Robin plugged in a rogue switch to an unused port in the LAN with a priority lower than any other switch inthe network so that he could make it a root bridge that will later allow him to sniff all the traffic in thenetwork.
What is the attack performed by Robin in the above scenario?
A . ARP spoofing attack
B . VLAN hopping attack
C . DNS poisoning attack
D . STP attack
Answer: C
Explanation:
Domain Name Server (DNS) spoofing (a.k.a. DNS cache poisoning) is an attack in which altered DNS records are used to redirect online traffic to a fraudulent website that resembles its intended destination.
Once there, users are prompted to login into (what they believe to be) their account, giving the perpetrator the opportunity to steal their access credentials and other types of sensitive
information. Furthermore, the malicious website is often used to install worms or viruses on a user’s computer, giving the perpetrator long-term access to it and the data it stores.
Methods for executing a DNS spoofing attack include:
✑ Man in the middle (MITM)C The interception of communications between users and a DNS server in order to route users to a different/malicious IP address.
✑ DNS server compromiseC The direct hijacking of a DNS server, which is configured to return a malicious IP address.
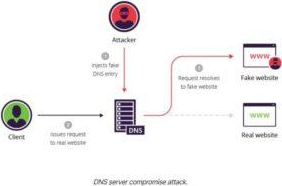
switch
DNS cache poisoning exampleThe following example illustrates a DNS cache poisoning attack, in which an attacker (IP 192.168.3.300) intercepts a communication channel between a client (IP 192.168.1.100) and a server computer belonging to the website www.estores.com (IP 192.168.2.200).
In this scenario, a tool (e.g., arpspoof) is used to dupe the client into thinking that the server IP is 192.168.3.300. At the same time, the server is made to think that the client’s IP is also 192.168.3.300.
Such a scenario would proceed as follows:
✑ The attacker uses arpspoof to issue the command: arpspoof 192.168.1.100 192.168.2.200. This modifies the MAC addresses in the server’s ARP table, causing it to think that the attacker’s computer belongs to the client.
✑ The attacker once again uses arpspoof to issue the command: arpspoof 192.168.2.200 192.168.1.100, which tells the client that the perpetrator’s computer is the server.
✑ The attacker issues the Linux command: echo 1> /proc/sys/net/ipv4/ip_forward. As a result, IP packets sent between the client and server are forwarded to the perpetrator’s computer.
✑ The host file, 192.168.3.300 estores.com is created on the attacker’s local computer, which maps the website www.estores.com to their local IP.
✑ The perpetrator sets up a web server on the local computer’s IP and creates a fake website made to resemble www.estores.com.
✑ Finally, a tool (e.g., dnsspoof) is used to direct all DNS requests to the perpetrator’s local host file. The fake website is displayed to users as a result and, only by interacting with the site, malware is installed on their computers.

Leave a Reply