Posted by: Pdfprep
Post Date: December 4, 2020
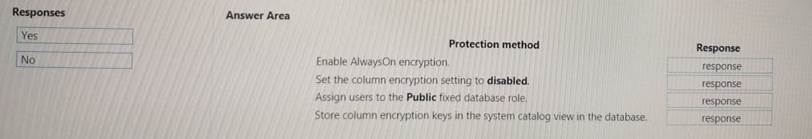
You maintain an Azure SQL Database instance. Management 01 the database is performed by an external party. All cryptographic keys are stored in an Azure Key Vault.
You must ensure that the external party cannot access the data in the SSN column of the Person table.
Which each protection method meet the requirement? To answer. drag the appropriate responses to the correct protection methods. Each response may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Answer:

Leave a Reply