Click the Exhibit button.
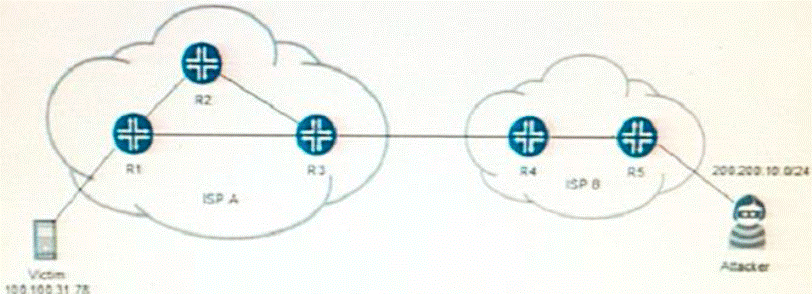
Referring to the network shown in the exhibit, a SYN flood attacks is initiated by an attacker that has a public IP address from ISP B within the 200.200.10.0/24 prefix The attacker Is sending SYN packets to the victim, connected to ISP A, with destination address of 100.100.31.78 using spoofed source addresses at random from the 192 1680.0/16 prefix.
Which two design best practices would prevent this attack from working? (Choose two)
A . ISP A should implement an ingress firewall filler on router R2 lo discard traffic originating from the 200.200.10.0/24 prefix
B . ISP A should implement an ingress firewall filer on router R3 to discard traffic originating from the 192. 168.0.0/16,172 16.0.0/12, and 10.0.0.0/8 prefixes
C . ISP A should implement an ingress firewall filter on router R3 to discard traffic originating from the 200.200.10.0/24 prefix
D . ISP B should implement an ingress firewall filer on the router R5 interface connecting to the attacker that discards packets with a source address not matching the 200.200.10 0/24 prefix.
Answer: B,D

Leave a Reply