Posted by: Pdfprep
Post Date: March 11, 2021
Refer to the exhibit.
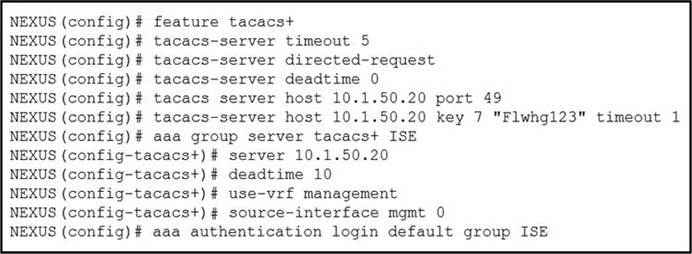
What is the result of implementing this configuration?
A . The TACACS+ server uses the type-6 encrypted format.
B . The switch queries the TACACS+ server by using a clear text PAP login.
C . The timeout value on the TACACS+ server is 10 seconds.
D . The switch queries the TACACS+ server by using an encrypted text PAP login.
Answer: B
Explanation:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus9000/sw/93x/security/con figuration/guide/b-cisco-nexus-9000-nx-os-security-configuration-guide-93x/b-cisco-nexus-9000-nx-os-security-configuration-guide-93x_chapter_011.html
The command "deadtime" is in minutes, not in seconds.
![]()

Leave a Reply