An organization allows the use of open-source software as long as users perform a file integrity check on the executables and verify the file against hashes of known malware.
A user downloads the following files from an open-source website:
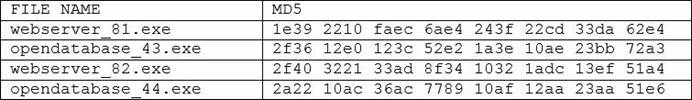
After submitting the hashes to the malware registry, the user is alerted that 2f40 3221 33ad 8f34 1032 1adc 13ef 51a4 matches a known malware signature. The organization has been running all of the above software with no known issues.
Which of the following actions should the user take and why?
A . Download and run the software but notify the organization’s cybersecurity office. The malware registry has a false positive since the software has been running without any issues.
B . Do not run any of the software and notify the organization’s cybersecurity office. The open-source website has been compromised, and none of the software can be trusted.
C . Download and run only webserver_82.exe and opendatabase_44.exe and notify the organization’s cybersecurity office. Legacy versions of the software have been compromised.
D . Do not run webserver_82.exe and notify the organization’s cybersecurity office. The software is malware.
Answer: D

Leave a Reply