Refer to the exhibit.
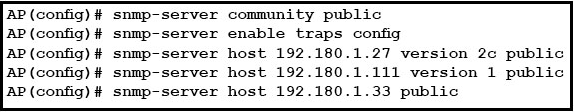
Which option describes what this sequence of commands achieves on a Cisco Autonomous AP?
A . This example shows how to permit any SNMP manager to access all objects with read-only permission using the community stringpublic. The access point also sends config traps to the hosts 192.180.1.111 and 192.180.1.33 using SNMPv1 and to the host 192.180.1.27 using SNMPv2
B . The community stringpublicis sent with the traps.
C . This example shows how to permit any SNMP manager to access all objects with read-only permission using the community stringpublic. The access point also sends config traps to the hosts 192.180.1.111 and 192.180.1.33 using SNMPv1 and to the host 192.180.1.27 using SNMPv2
D . The community stringpublicis not sent with the traps as this is the default.
E . This example shows how to permit any SNMP access to all objects with read-only permission to only three specific IP addresses using the community stringpublic.The access point also sends config traps to the hosts 192.180.1.111 and 192.180.1.33 using SNMPv1 and to the host 192.180.1.27 using SNMPv2
F . The community stringpublicis sent with the traps.
G . This example shows how to permit any SNMP access to all objects with read-only permission to only three specific IP addresses using the community stringpublic.The access point also sends config traps to the hosts 192.180.1.111 and 192.180.1.33 using SNMPv1 and to the host 192.180.1.27 using SNMPv2
H . The community stringpublicis not sent with the traps.
Answer: A
Explanation:
SNMPv1 and SNMPv2 use the notion of communities to establish trust between managers and agents. An agent is configured with three community names: read-only, read-write, and trap. The community names are essentially passwords; there’s no real difference between a community string and the password you use to access your account on the computer. The three community strings control different kinds of activities. As its name implies, the read-only community string lets you read data values, but doesn’t let you modify the data. For example, it allows you to read the number of packets that have been transferred through the ports on your router, but doesn’t let you reset the counters. The read-write community is allowed to read and modify data values; with the read-write community string, you can read the counters, reset their values, and even reset the interfaces or do other things that change the router’s configuration. Finally, the trap community string allows you to receive traps (asynchronous notifications) from the agent.
Most vendors ship their equipment with default community strings, typicallypublicfor the read-only community andprivatefor the read-write community. It’s important to change these defaults before your device goes live on the network. (You may get tired of hearing this because we say it many times, but it’s absolutely essential.) When setting up an SNMP agent, you will want to configure its trap destination, which is the address to which it will send any traps it generates. In addition, since SNMP community strings are sent in clear text, you can configure an agent to send an SNMP authentication-failure trap when someone attempts to query your device with an incorrect community string. Among other things, authentication-failure traps can be very useful in determining when an intruder might be trying to gain access to your network.
Because community strings are essentially passwords, you should use the same rules for selecting them as you use for Unix or NT user passwords: no dictionary words, spouse names, etc. An alphanumeric string with mixed upper- and lowercase letters is generally a good idea. As mentioned earlier, the problem with SNMP’s authentication is that community strings are sent in plain text, which makes it easy for people to intercept them and use them against you. SNMPv3 addresses this by allowing, among other things, secure authentication and communication between SNMP devices.
Reference:
http://docstore.mik.ua/orelly/networking_2ndEd/snmp/ch02_02.htm

Leave a Reply