Refer to the exhibit.
If a supplicant supplies incorrect credentials for all authentication methods configured on the switch, how will the switch respond?
A . The supplicant will fail to advance beyond the webauth method.
B . The switch will cycle through the configured authentication methods indefinitely.
C . The authentication attempt will time out and the switch will place the port into the unauthorized state.
D . The authentication attempt will time out and the switch will place the port into VLAN 101.
Answer: A
Explanation:
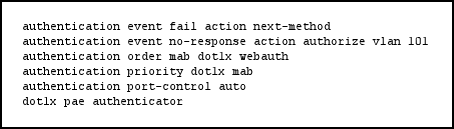
Flexible authentication (FlexAuth) is a set of features that allows IT administrators to configure the sequence and priority of IEEE 802.1X, MAC authentication bypass (MAB), and switch-based web authentication (local WebAuth). Case 2: Order MAB Dot1x and Priority Dot1x MAB If you change the order so that MAB comes before IEEE 802.1X authentication and change the default priority so that IEEE 802.1X authentication precedes MAB, then every device in the network will still be subject to MAB, but devices that pass MAB can subsequently go through IEEE 802.1X authentication. Special consideration must be paid to what happens if a device fails IEEE 802.1X authentication after successful MAB. First, the device will have temporary network access between the time MAB succeeds and IEEE 802.1X authentication fails.
What happens next depends on the configured event-fail behavior. If next-method is configured and a third authentication method (such as WebAuth) is not enabled, then the switch will return to the first method (MAB) after the held period. MAB will succeed, and
the device will again have temporary access until and unless the supplicant tries to authenticate again. If next-method failure handling and local WebAuth are both configured after IEEE 802.1X authentication fails, local WebAuth ignores EAPoL-Start commands from the supplicant.
MAB –>MAB Pass–> Port Authorized by MAB –> EAPoL-Start Received –> IEEE 802.1x MAB –>MAB Fail–> IEEE 802.1x (config-if)#authentication order mab dot1x (config-if)#authentication priority dot1x mab
Source: http://www.cisco.com/c/en/us/products/collateral/ios-nx-os-software/identity-basednetworking-service/ application_note_c27-573287.html

Leave a Reply